Knowledge base article
Recover your hacked WordPress website
Related articles
Basic WordPress security and site management
Create a SSH key pair and configure your SSH key in cPanel
How did my WordPress website get hacked? What do I do?
Other cpanel articles
A beginners guide to email spoofing
Accessing your site before changing DNS
An introduction to email authentication
Basic WordPress security and site management
Can I test out your services for free?
Check MySQL database table disk usage
Configure object cache with memcached and Litespeed Cache plugin
Configure spam filtering in cPanel
Configure your cPanel email account in Gmail
Connect via SFTP using SSH key authentication with FileZilla
Connecting to Serversaurus shared hosting via SFTP
Create a clone of your website
Create a SSH key pair and configure your SSH key in cPanel
Create a WordPress administrator via MySQL CLI
Create a WordPress administrator via phpMyAdmin
Create a WordPress cron task in cPanel
Create and manage email accounts in cPanel
Create Autoresponders in cPanel
Disable automatic WordPress updates via wp-config.php
Domain options for shared hosting
Download or restore individual files, directories or database backups with JetBackup
Emptying Trash, Junk and Spam files
Enabling PHP extensions, Changing PHP Version and Setting PHP Options
Export or Import a MySQL database via CLI
Force HTTPS via .htaccess (cPanel)
Go live with your WordPress staging website
Help! I need a backup of my cPanel-hosted website
Hide .html extension using .htaccess
How did my WordPress website get hacked? What do I do?
How to ensure website generated emails are delivered successfully
How to issue a Let’s Encrypt certificate
How to remove Site Software management
I can receive email but can’t send!
Install and configure Ghost blog in cPanel using Apache Reverse Proxy with mod_proxy
Install or manage complimentary SSL certificates with AutoSSL
Introduction to LiteSpeed Cache
Login to cPanel via the Client Portal
Manage DNS zones with the cPanel Zone Editor
Manual WordPress migrations in a nutshell
Migrate remote staging website to local hosting server
Migrate remote transactional website to local server
Migrating email from one POP/IMAP email account to another
My site and/or email service is down
Network Firewall (I can’t access my services on a non-standard port)
Pointing your domain to Serversaurus
Pointing your domain to Squarespace with cPanel
Prevent website generated spam with CAPTCHA
Push updates from a staging to production website
Reconfigure production website to subdomain
Remove Wordfence firewall block via MySQL CLI
Secure your WordPress installation
Setting up email on your iPhone
Subdomains for test sites & more
The SLA – Best effort versus 99.9% versus 100%
Unable to renew certificate: The Let’s Encrypt HTTP challenge failed
Understanding CloudLinux resource limits
Update a WordPress website to use a new domain name
Update your WordPress username via phpMyAdmin
What exactly is shared hosting?
Why don’t you have unlimited plans?
WordPress install still shows Serversaurus “new customer” landing page
This article will teach you how to restore your hacked WordPress website
If you are reading this page you are most likely, most unfortunately, hacked! Thankfully its relatively straight forward to restore your website to its former glory.
To learn about common causes for a website becoming hacked, please read our guide about common vulnerabilities which also includes recommendations for prevention.
- Firstly, if your website is redirecting to a fraud/spam website when visiting the domain in your browser, it's likely your database has been injected with the fraudulent domain name, if you are experiencing this redirect issue, lets start by checking the site_url is set correctly in the database.
To check and/or update the site_url, login to cPanel and navigate to the phpMyAdmin function. You will see your hosted databases on the left hand side of phpMyAdmin, select your database to view the tables (if you don't know which one is your live site, please check the database name stated in the sites wp-config.php file).
Now you're viewing the database tables, select the table labelled wp_options. At the top of the wp_options table take note of the top two rows, siteurl and home. These fields dictate the domain name the application uses, please check whether these are set to use the correct domain name, if not you can click in the text field to update the domain name.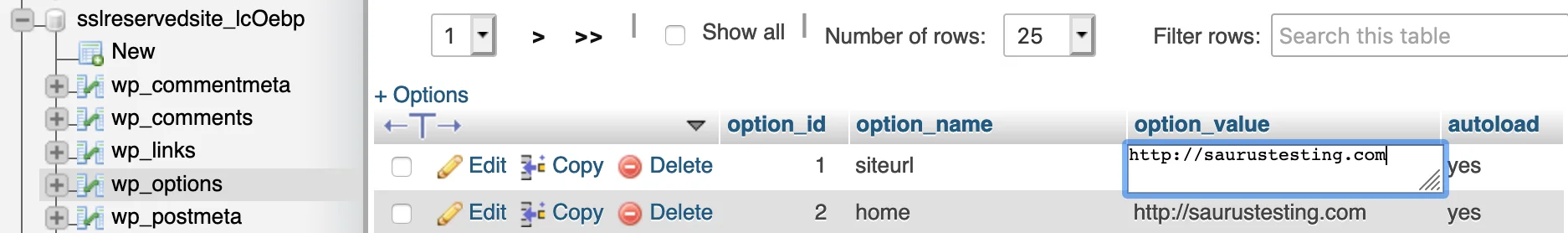
Now check if you can access the website again, if so- please continue to step 3- if the website is still appearing compromised, please continue to step 2. - We need to reinstall WordPress core to ensure the application files are "clean" (you can process this step via WordPress dashboards automated update tools if you are unable).
If you are unable to access WordPress dashboard, follow the below steps to reinstall WordPress manually
2a. SSH onto your hosting server. Replace the username and server field with your cPanel username and the name of your server. You can find these details in your Welcome to Serversaurus Business Hosting email. Enter your password at the prompt to log in.ssh username@server.serversaurus.com.au
2b. Using the wget command, we will download the latest WordPress version into our current directory.
wget http://wordpress.org/latest.tar.gz
Now to extract the contents of the latest.tar.gz file type the command:
tar xfz latest.tar.gz
2c. Change into the directory where your current WordPress site is installed.Note: This can differ depending on your setup, if these updates are for your primary website WordPress will most likely be installed under public_html.
To change into your public_html directory type and enter:
cd public_html
If you are reinstalling WordPress under an addon domain, navigate to the addon domain's home directory using the below command:
cd yourdomainname.com
2d. Now we want to copy the files/directories which are unique to your website and move them into the directory with your fresh WordPress install overwriting default directories or files that were included in the installation.
Use the below command to recursively copy your unique website files:
cp -r wp-content/ wp-config.php .htaccess ~/wordpress
2e. Next we'll remove the existing WordPress installation from the current directory
rm -fr ./*
2f. The final step is to move the new WordPress files with your content into the current directory.
mv ~/wordpress/* .
2h. Now let's tidy up after ourselves, we no longer need the WordPress directory or the latest.tar.gz file, to remove these items, issue the following command:
rm -f ~/latest.tar.gz ~/wordpress/ - Login to WordPress dashboard as before, and install WordFence (if you have not already). Then immediately run the WordFence scan, the scan will identify whether there are further compromised files and offers a tool to remove the compromised file/s, needless to say, use the tool to remove any compromised files until you receive a 100% clean scan result.
This step is important, as although you have reinstalled WordPress core, it's possible plugin or theme files could have malicious code which was not "cleaned" when reinstalling WordPress core files. - Update all WordPress user passwords!!!
You website should now be completely clean of malicious code (wippee!). If you want to take further precautions to prevent becoming hacked in the future, please complete our recommendations in our WordPress security and management guide, and for more advanced recommendations, please refer to our guide about securing a WordPress installation.
Published August 24, 2020. Last updated November 30, 2023.
Can't find what you're looking for?
"*" indicates required fields